
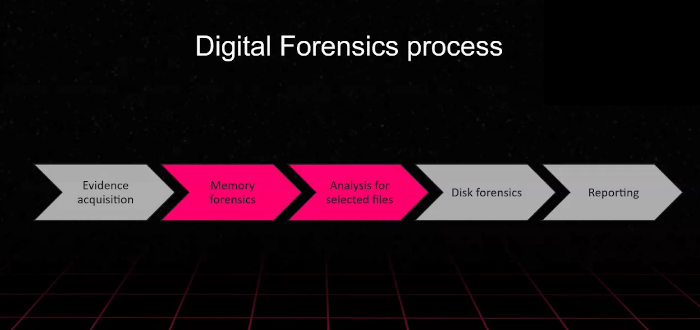
Practical Digital Forensics: Forensic Lab Setup, Evidence Analysis, and Structured Investigation Across Windows, Mobile, Browser, HDD, and Memory (English Edition): Bhardwaj, Dr. Akashdeep, Kaushik, Keshav: 9789355511454: Amazon.com: Books
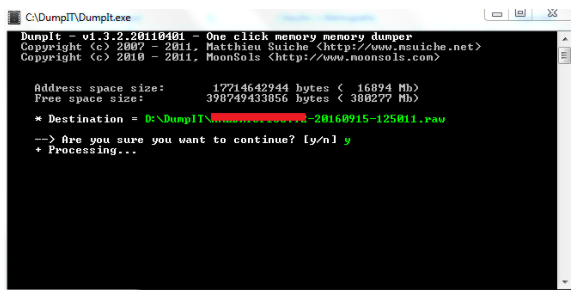
Digging up memories – a deep-dive into memory forensics in the Cyber Security Essentials meetup | Nixu Cybersecurity.





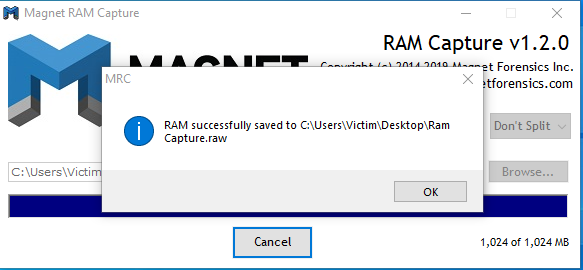
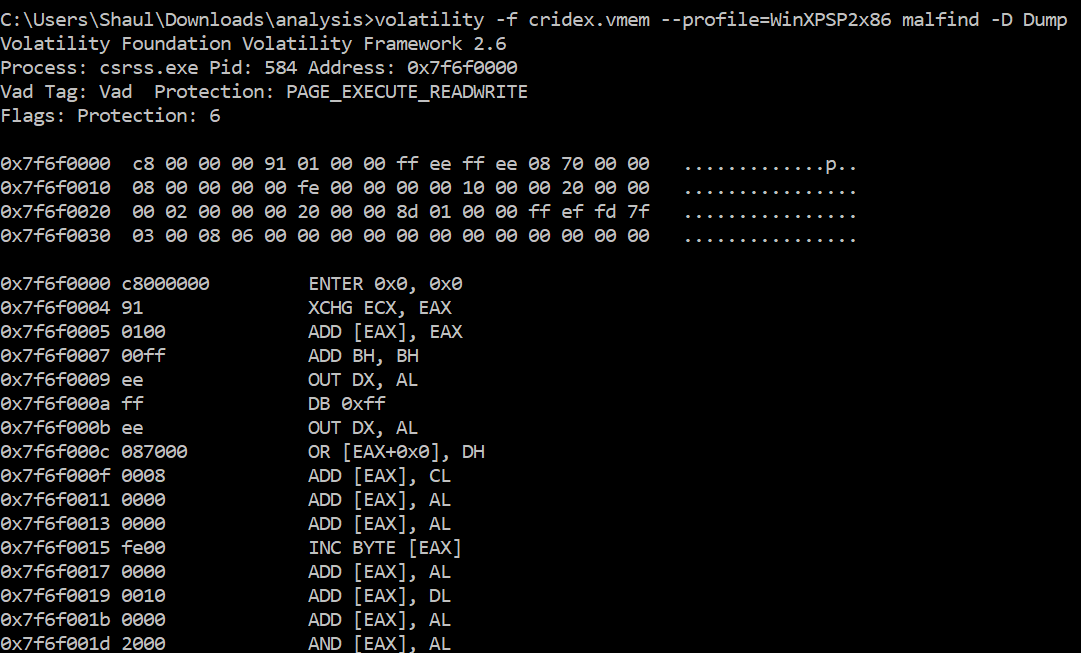


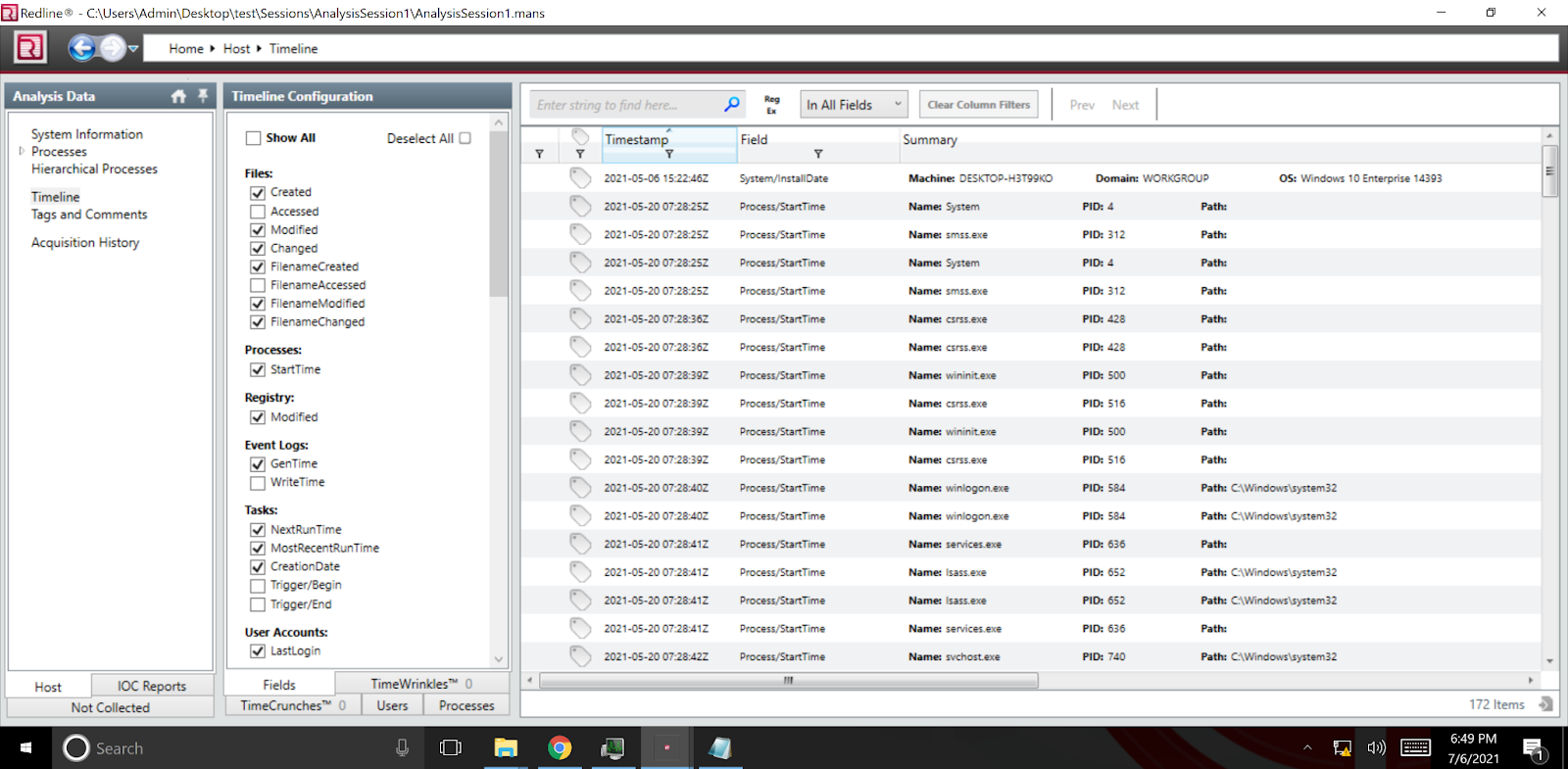


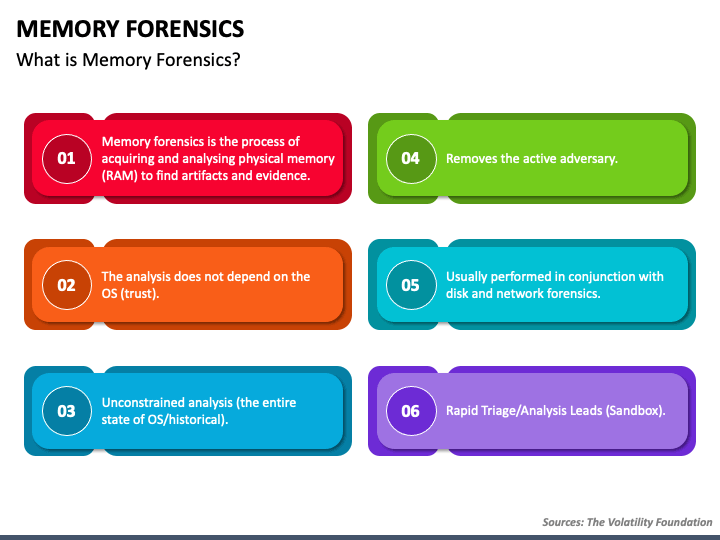



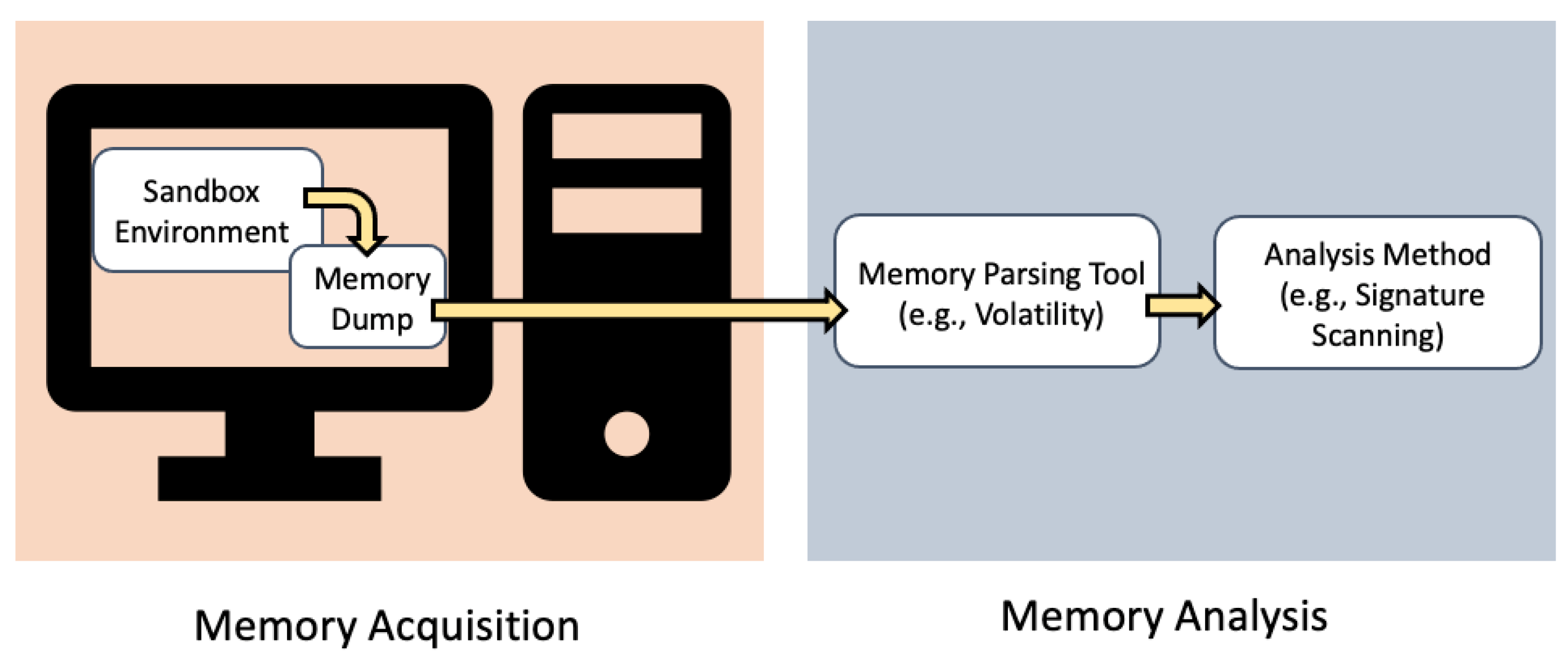

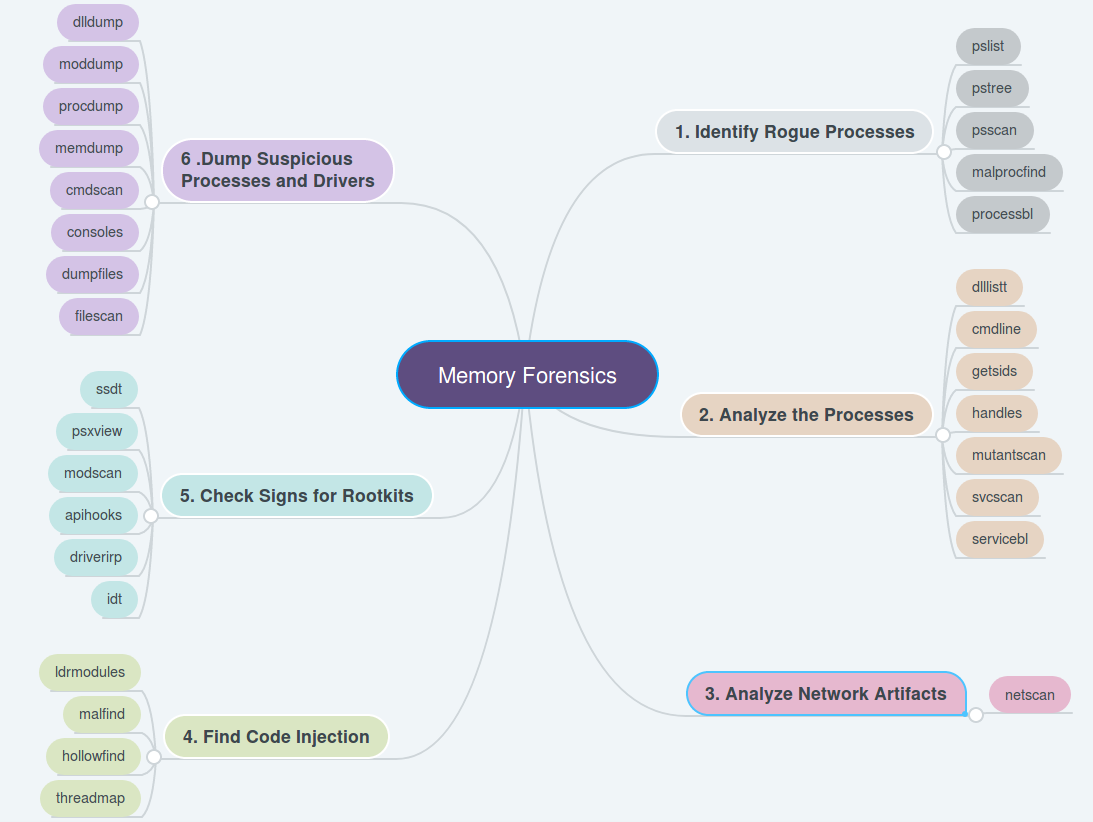
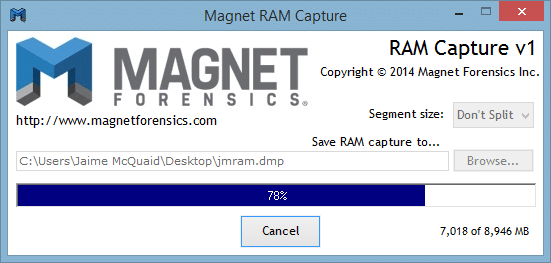
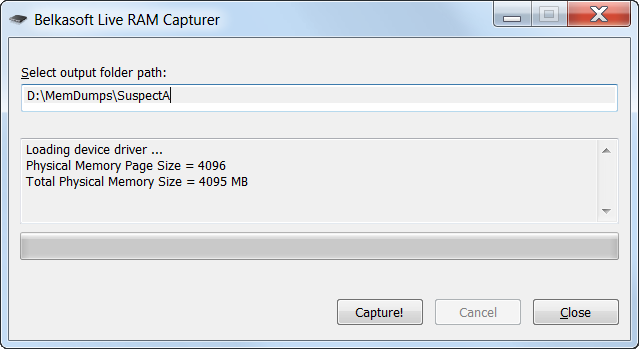
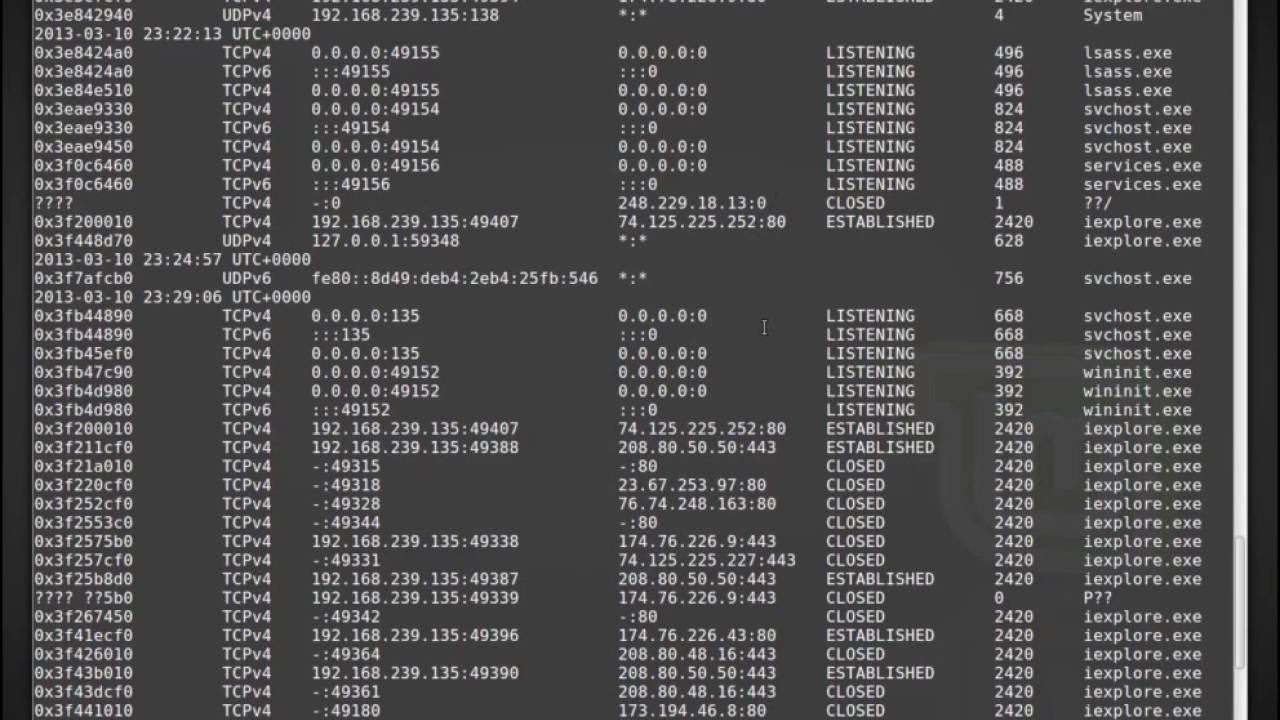

![PDF] Memory Forensics: Review of Acquisition and Analysis Techniques | Semantic Scholar PDF] Memory Forensics: Review of Acquisition and Analysis Techniques | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5844da2c4456091748958bcc035ff8a52e6d8340/18-Figure1-1.png)
