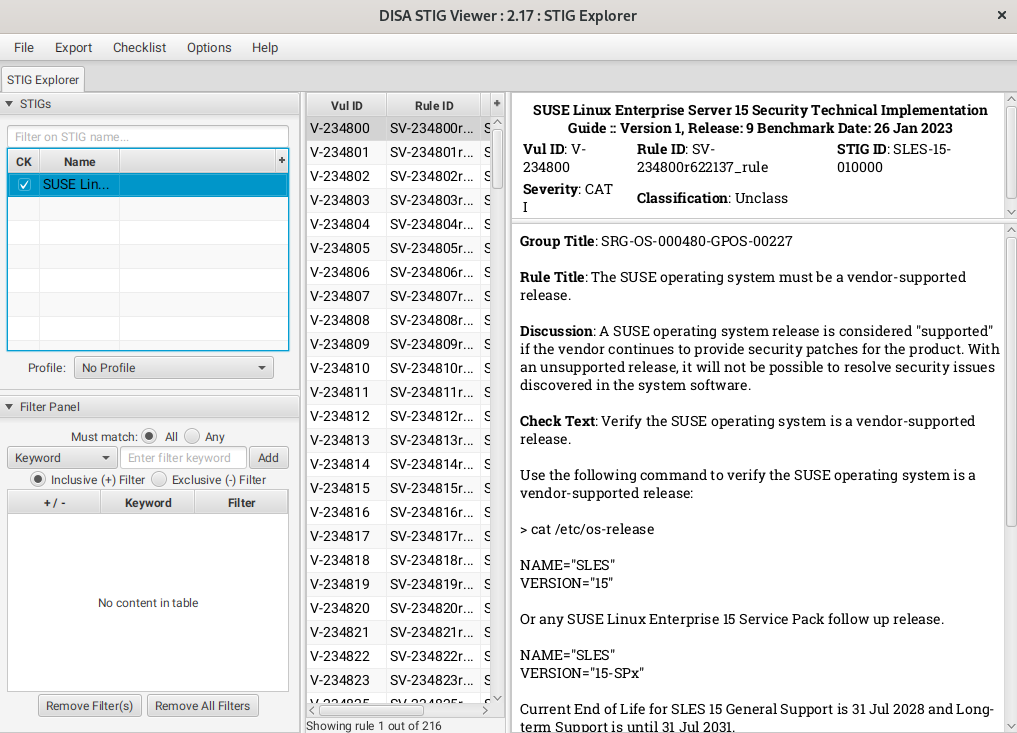
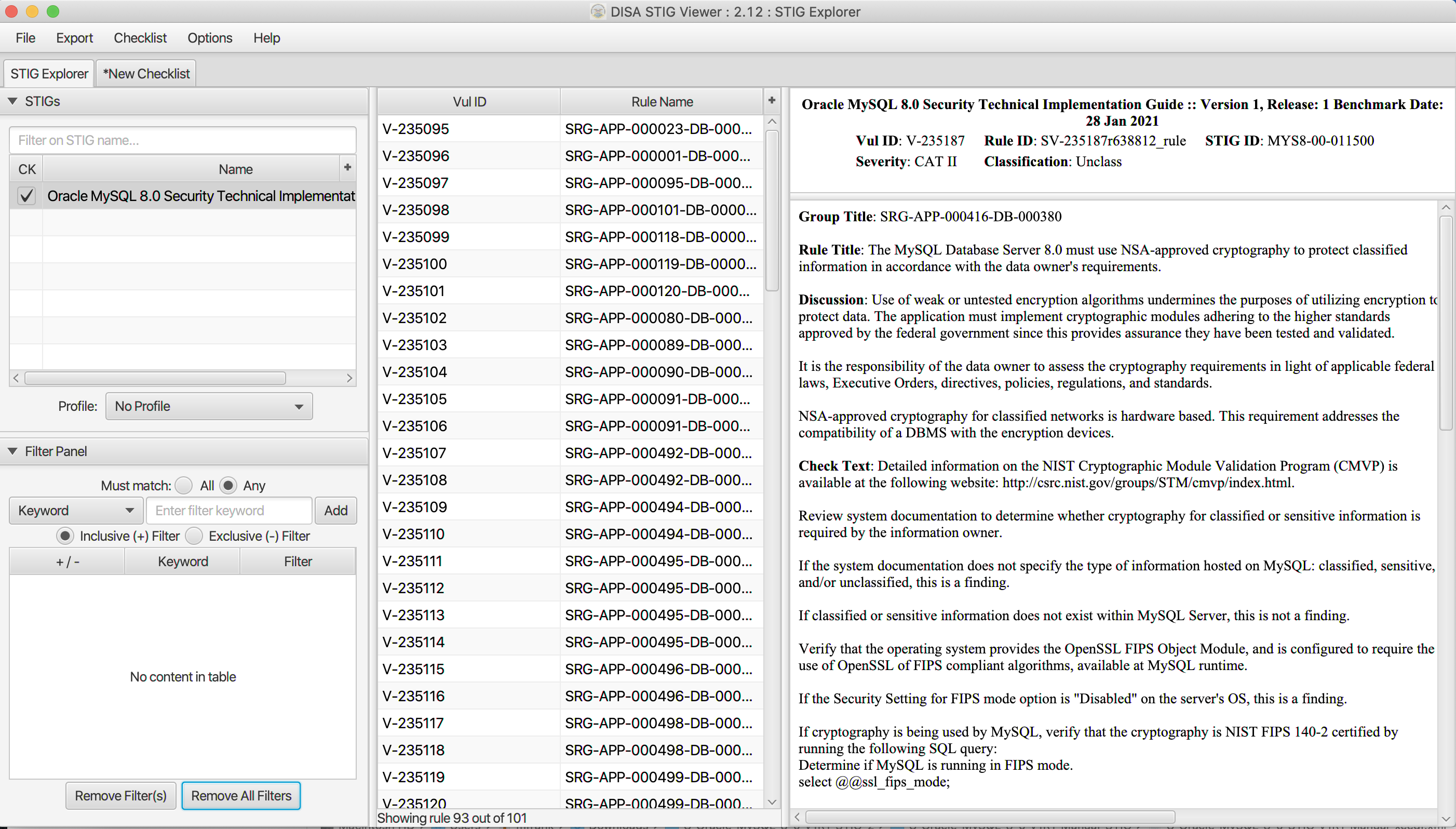
How to use DoD Cyber Exchange - STIGs (Secure Technical Implementation Guides) and STIG Viewer App - Operating Systems
Defense Security Service Industrial Security Field Operations National Industrial Security Program (NISP) Authorization Office

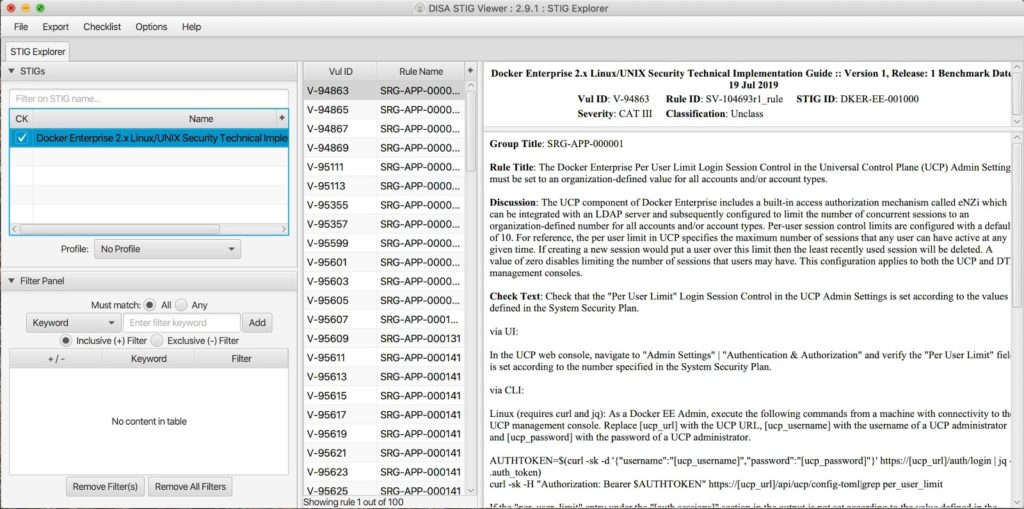
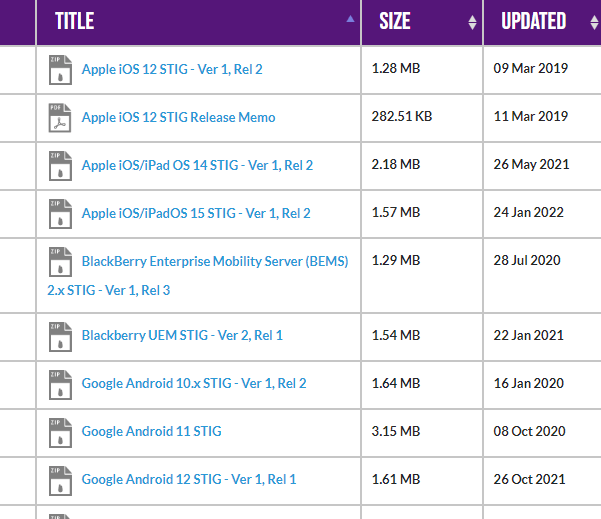
How to use DISA STIG Viewer Tool. DISA STIG Viewer is a GUI java based… | by Tutela Security | Medium